Whether it’s our accounts on social media platforms, our accounts on other websites, or even directly the operating system of our mobile devices, we must create strong and unique passwords for their security. However, no matter how strong your password is, when you want to talk about real security, you should use the two-factor authentication feature called 2FA.
Two-factor authentication, in its simplest definition, is a double password. In other words, even if someone knows the password of your account, they cannot log into your account unless they have your phone because a one-time password comes to your phone to log in. You will understand that a very simple but extremely effective security is important. Let’s take a closer look at what two-factor authentication is.
What is Two-Factor Authentication?
Two-factor authentication, patented in 1984 and referred to as 2FA, is a security measure used to confirm user identity. When we look at the patent year, we can see that there was a need for security even years before the widespread use of computers and the internet.
The working principle of the two-factor authentication system is simple. Whether it is a bank or social media account, a password is sent by the system to the mobile phone that only the user can access, apart from the account password, for proof of identity. This password is for one use only and is considered a password known only to the account owner, unless the phone has been stolen or the owner has been kidnapped.
Are 2FA apps safe?
Yes, authentication apps have a high degree of security. Authentication apps are considered a more secure 2FA method than codes sent via SMS. They generally tend not to be dependent on the internet or mobile connections, which means that there is nothing for attackers to get their hands on. Instead, codes are generated directly on your device. Also, authentication apps don’t have access to your accounts, they just generate code.
How do authentication apps work without an internet connection? With a process called hashing. Hashing is a type of encryption that uses an algorithm for the purpose of generating unique code. However, unlike ‘encryption’, which is decipherable in nature, hashing is not reversible. In order for the authentication process to be successful, it must be proven that the generated code is a result of this algorithm.
The Best 2FA Apps for iPhone and Android
Today, two-factor authentication applied on mobile devices can be done simply and securely through mobile apps. In this list, we’ve brought together the best 2FA apps you can use on your iPhone and Android devices.
- Google Authenticator
- Twilio Authy
- LastPass Authenticator
- Microsoft Authenticator
- Duo Mobile
- 2FA Authenticator (2FAS)
Google Authenticator
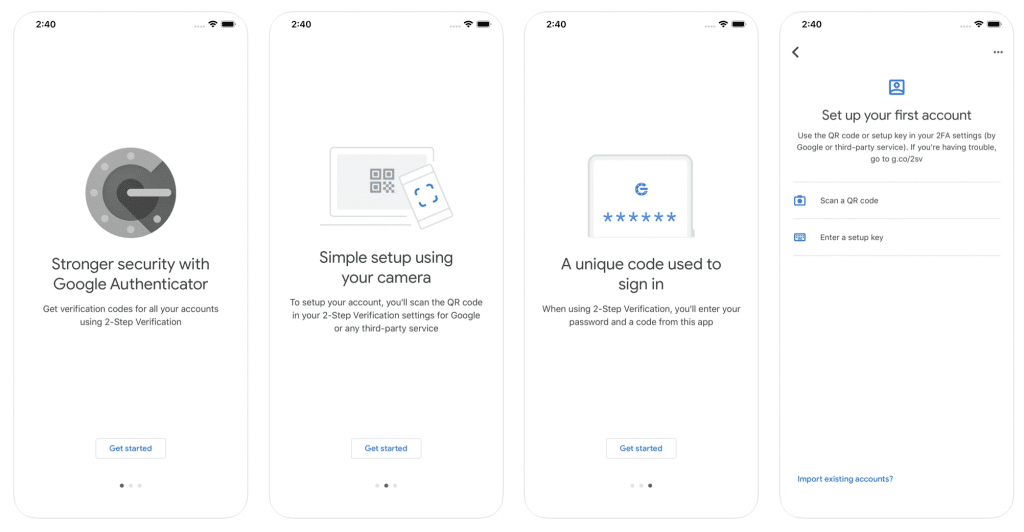
The most popular authenticator app with TOTP and HOTP algorithms gives you a real-time authentication code that changes every 30 seconds.
Google Authenticator is a practical solution if you don’t want to deal with token synchronization via the cloud. The app allows you to easily export all the tokens created in it into one large QR code and import from there to a new device. In the iOS version, tokens can now be searched and access to the app can be restricted by fingerprint and facial recognition. Besides, there is no search or protection feature in the Android version.
You don’t need to create an account to access the app which has a quite simple user interface. The app also has a Chrome Extension.
Pros:
- No phone number required
- Can be used without an account
- Easy to use interface
- Various third-party integrations
Cons:
- Does not hide codes
- No multiple device support
- There is no access protection to the app
- Not open source
Google Authenticator on the App Store
Google Authenticator on Google Play
Twilio Authy
As one of the best authenticator apps, Twilio Authy provides full cross-platform support as well as advanced 2fa features. The app has separate versions for all operating systems, and it allows these versions to be easily synchronized with each other.
With Authy, one of its biggest advantages is encrypted cloud backup, you can use the option to enter a custom password or passphrase that it uses to encrypt logins for your accounts in the cloud.
The app’s interface looks different from other authenticators. Instead of a list, a series of tabs appears on the screen. Only one selected token can be viewed at any given time. Others appear as small icons at the bottom of the screen. You can switch between these icons. If you have many tokens, your job gets a little harder.
Pros:
- Available on various platforms
- Authentication by SMS, email and phone
- Free support
- Various third-party integrations
Cons:
- Up to 100 authentication transactions per month
- Phone number required to create an Authy account
Also Read: The Best Password Managers for iPhone
Also Read: The Best Password Managers for Android
LastPass Authenticator
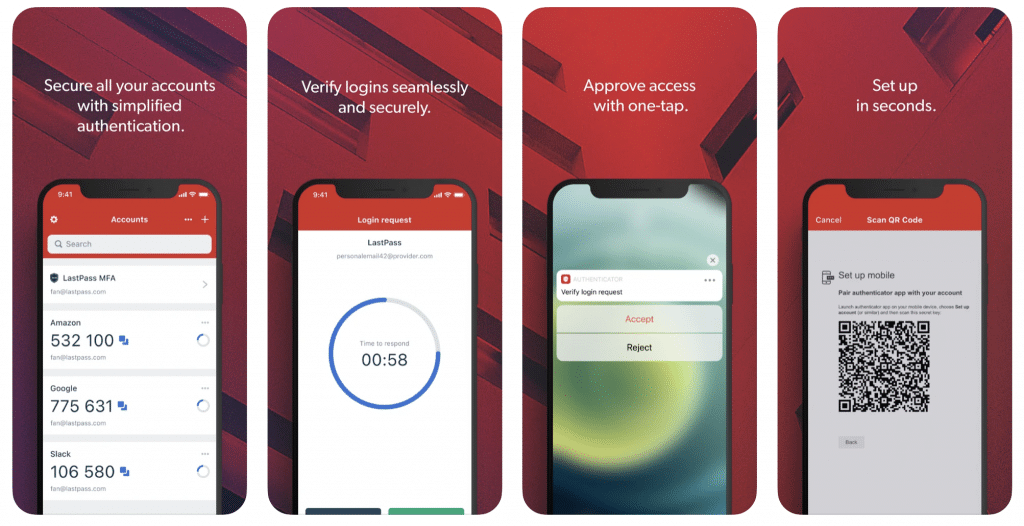
Getting started with LastPass Authenticator, a standalone app separate from the LastPass password manager app, is pretty easy if you already have a LastPass account. The trusted app supports TOTPs as well as push notification-based verification for Amazon, Evernote, Google, Dropbox, and Facebook.
The app, which generates 6-digit codes every 30 seconds, also provides support for other TOTP compatible services and apps such as Google Authenticator.
Pros:
- Works seamlessly if you already use LastPass for password management.
- Compatible with any site/app that uses standard Time-based One-Time Passwords (like Google Authenticator).
- Offers convenient push-based 2FA for LastPass logins — faster than entering a code manually.
- Can back up your 2FA tokens to your LastPass account, making it easier to restore them if you lose your phone.
Cons:
- The backup feature relies on you having a LastPass account — not ideal if you want a standalone authenticator.
- LastPass has had notable security incidents in recent years, which may make some users wary of consolidating 2FA with their vault.
- Lacks some features power users might want, like app lock, PIN protection, or biometric access specific to the Authenticator.
- Only works on mobile devices.
- Other sites won’t support push-based 2FA through this app.
LastPass Authenticator on the App Store
LastPass Authenticator on Google Play
Microsoft Authenticator
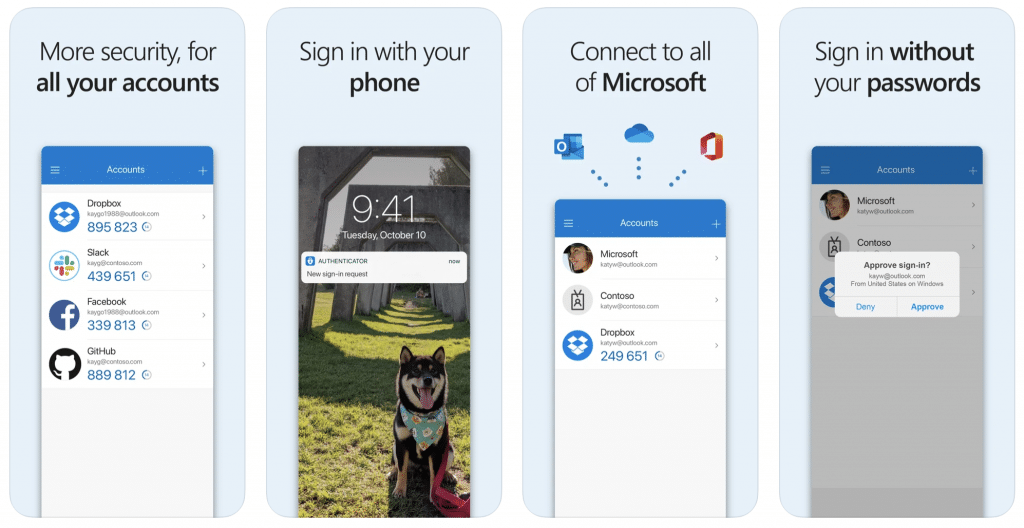
Microsoft Authenticator is one of the best authenticator apps that allows you to set a second layer of security for your accounts using multi-factor authentication, password autofill or passwordless.
Preferred by most people looking for an alternative to Google Authenticator, Microsoft’s app packs a few useful features alongside the basics. In the apps, the codes on the screen can be hidden, access to the app can be restricted on both iOS and Android versions, and tokens can be stored on the cloud. Microsoft Authenticator is also very useful if you work with Microsoft accounts frequently.
Pros:
- Access to the app can be restricted by PIN code, fingerprint or facial recognition
- Has cloud backup/sync
- Codes are hidden
- Available even if you don’t have an account (as long as you disable cloud backup)
- Microsoft makes signing in to accounts too simple
- iOS version supports Apple Watch
Cons:
- You need to log in to your Microsoft account for backup/sync on the Android version
- iOS and Android backup/sync systems are not compatible with each other
- Unable to export/import tokens
- Takes up a lot of space: 150-200 MB
Microsoft Authenticator on the App Store
Microsoft Authenticator on Google Play
Also Read: The Best Antivirus Apps for Android
Duo Mobile
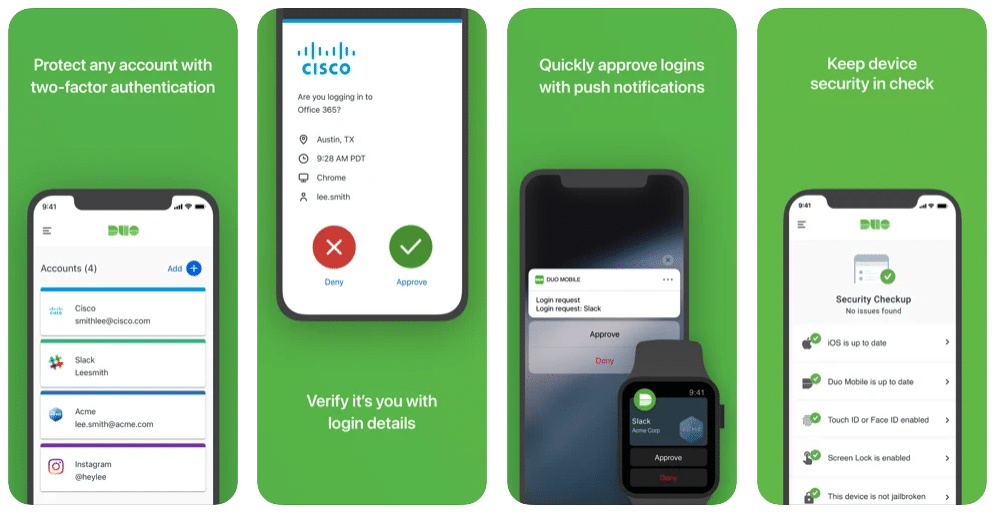
Duo Mobile, one of the best 2FA apps, was acquired by Cisco in 2018. Its biggest advantage is its simple and convenient interface. Duo Mobile also hides codes and you don’t need to create an account to use it. It generates passcodes for login and can receive push notifications for easy, one-tap authentication.
Duo Mobile uses two different systems for cloud backup, Google Cloud on Android and iCloud on iOS platform. For this, it makes use of the Google and Apple accounts that the smartphone user has already opened. So you don’t need to create a new account to use the app. However, this solution has a downside: you cannot sync data between Android and iOS versions. Duo Mobile does not support the export of files and there is no option to display a secret code or QR code for your previously saved tokens.
Pros:
- Simple and easy to use
- Hides codes
Cons:
- No app access protection
- Backup is difficult
2FA Authenticator (2FAS)
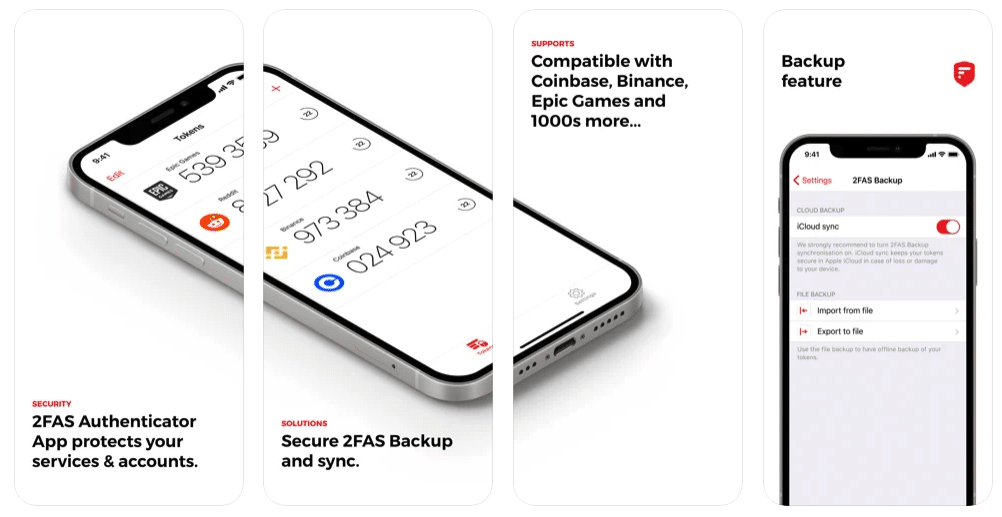
Last in our list of the best authenticator apps is 2FAS, a free app that generates time-based one-time passwords. The app also allows you to store all your tokens in the cloud to let you recover your keys if you lose your smartphone. Other notable features include device synchronization and Touch ID and Face ID authorization.
Pros:
- Simple and easy to use
- Various backup options (including cloud backup)
- Login security with PIN code and facial recognition
Cons:
- Limited documentation







Comments
Loading…